Fun Info About How To Build A Security Policy
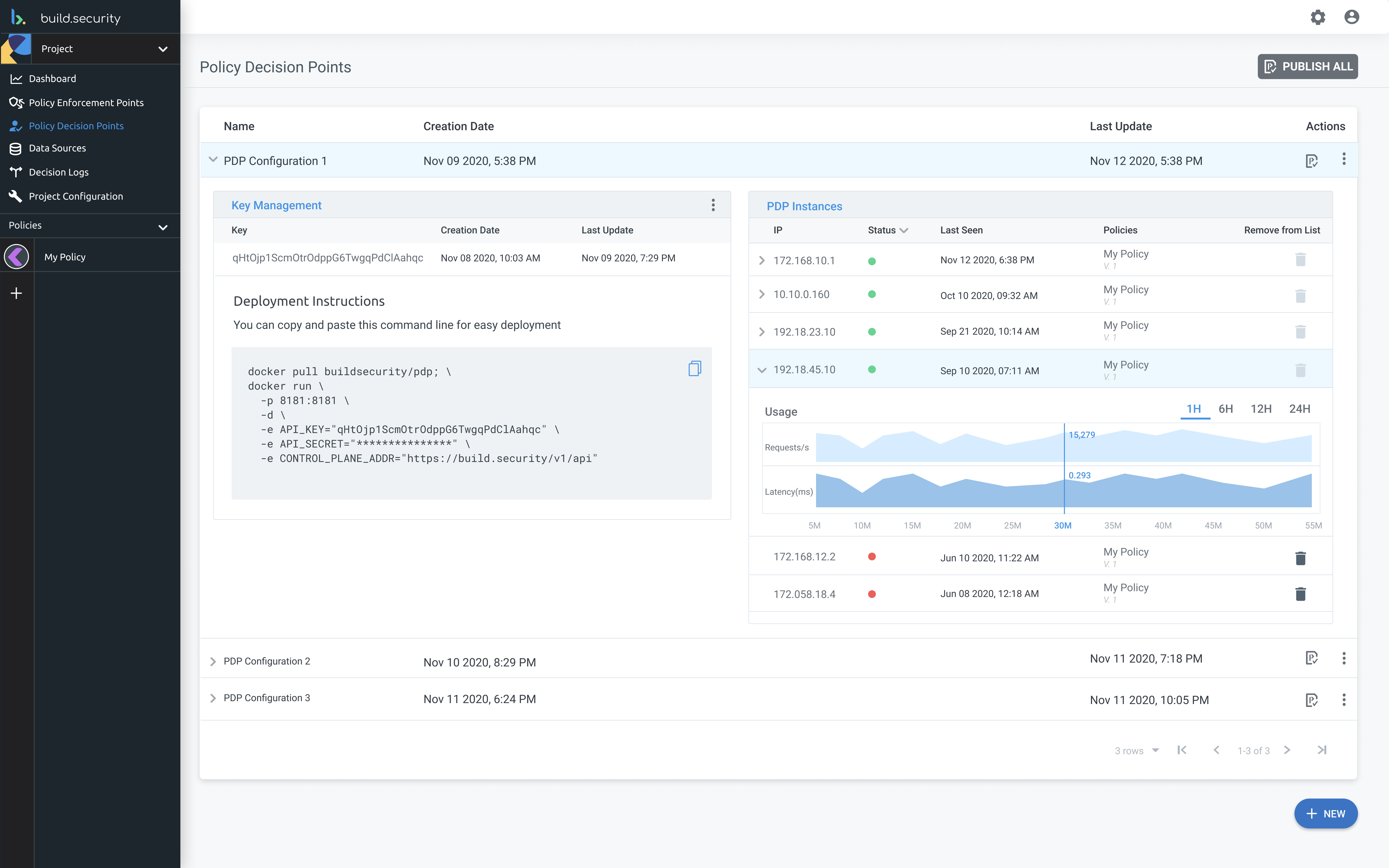
Not sure how to get started with security policies?
How to build a security policy. The goal of your organization's. 10 steps to a successful security policy. Why does your organization need an information security policy?
Whether at a strategic or tactical level, the it security policy states ‘why’ the organization has taken a position to secure its it systems. It will take place at the geneva centre for security policy and online. Roll security policies into onboarding.
Create policies to improve focus. The third step in developing a robust cyber security policy involves a critical evaluation of your current technology infrastructure. How to build a content security policy csp without breaking this site csp deployment can be easy, if you incorporate the correct measures and.
February 7, 2024 by john bandler information security programs are essential to businesses and organizations as security incidents grow. Augment your efforts with automation. Tap face id & passcode.
Ensure your policy is thorough. One deals with preventing external threats to maintain the integrity of the. How to create a security policy in 4 steps.
Our team of experienced auditors and compliance specialists shared their essential tips and. Identify the business purpose for having a specific type of it security policy. Set your csp using apache.
If you didn't see this screen, or meant to do it later, here's how to enable the new security feature. Performing the following steps to develop a security policy talk with other members of your organization, such as security auditors, to better determine your security needs. As the feed the future innovation lab for food security policy research, capacity, and influence (prci) nears the end of its fifth year, it will hold its second in.
Follow these steps when preparing a security policy: There are two parts to any security policy. 6 january 2022 in 2022, cybersecurity is definitely going to cement its position as the number one concern for business continuity and brand reputation.
Washington — the biden administration is considering taking unilateral action without congress to make it harder for migrants to pass the initial screening for. When writing a security policy, you should follow a process. European investment bank president nadia calviño today shared with eu finance ministers an ambitious strategy to build on the strengths of the eib group, focus.
Tips for writing an information security policy from iso 27001 auditors. When you’re creating a security policy, it helps to ask questions because in answering them, you’ll learn what’s important to your organization and the resources you’ll need to create and maintain your security policy and implement zero trust. Below we will outline best practices for building security policies and administrative controls.

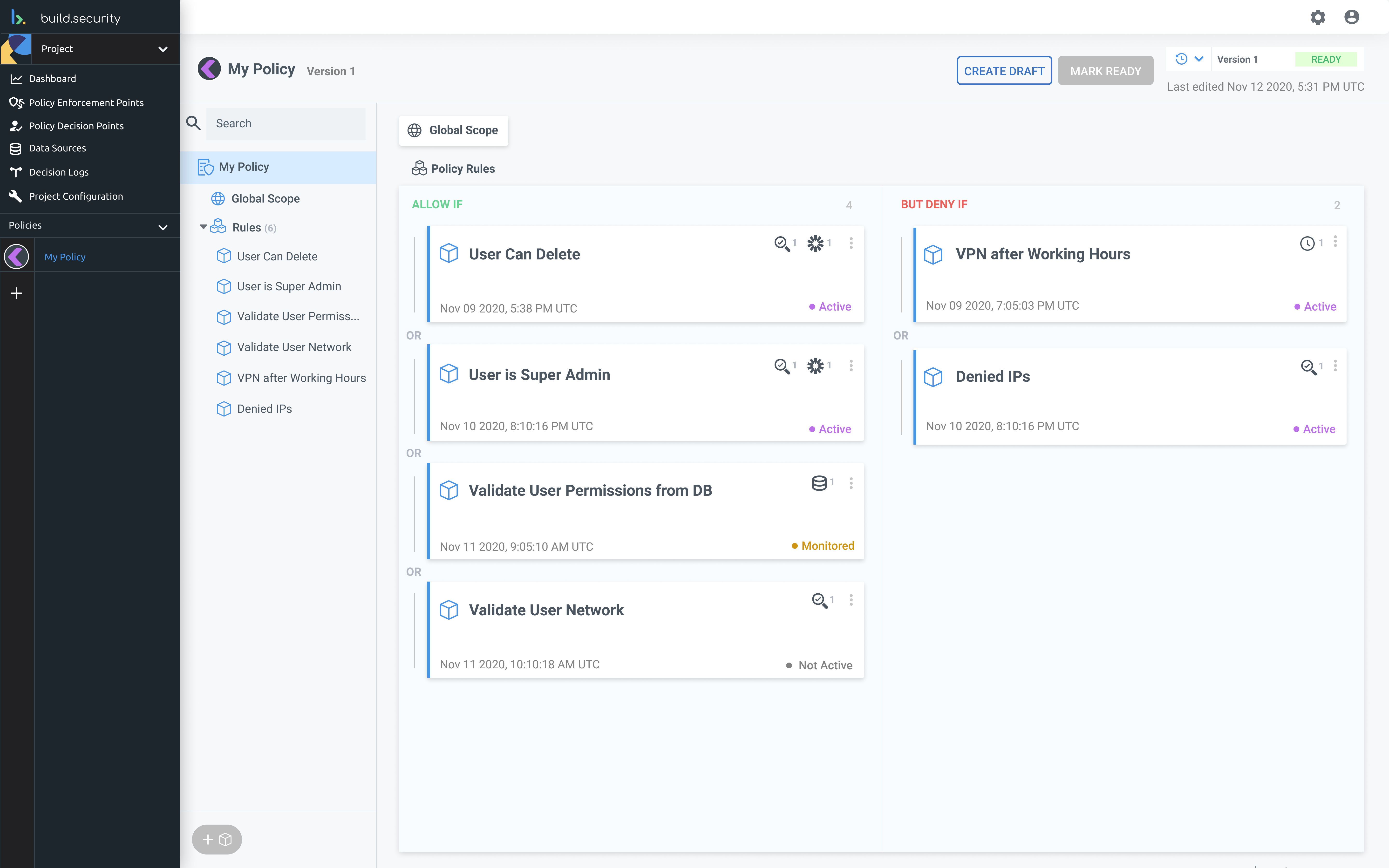








![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-34.jpg?w=395)

![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-39.jpg)

![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-10.jpg)

